

Google just released Chrome 79.0.3945.130 update, which will now detect certificates that attempt to exploit the NSA discovered CVE-2020-0601 CryptoAPI Windows vulnerability.
As part of Microsoft’s January 2020 Patch Tuesday, security updates were released for a vulnerability discovered by the NSA in the Windows CryptoAPI library Crypt32.dll.
This vulnerability allows attackers to create TLS and code-signing certificates that spoof, or impersonate, other companies to perform man-in-the-middle attacks or create phishing sites.
With PoCs for the CVE-2020-0601 vulnerability already released that allow attackers to easily create spoofed certificates, it is only a matter of time before we start to see them used in attacks.
The new version of Chrome blocks spoofed certificates
Today, Google released Chrome 79.0.3945.130, which adds new code by Google’s Ryan Sleevi to further check the integrity of a web site’s certificate before allowing a visitor to access the site.

Added CVE-2020-0601 detections to Google Chrome
To show the new protections at work, using Kudelski Security’s CVE-2020-0601 test site we can see the vulnerability being exploited on an unpatched Windows 10 PC using an older version of Google Chrome.

CVE-2020-0601 exploited in
On the same unpatched Windows 10 machine using Google Chrome 79.0.3945.130, when you visit the site again the browser now warns that “Attackers might be trying to steal your information”.
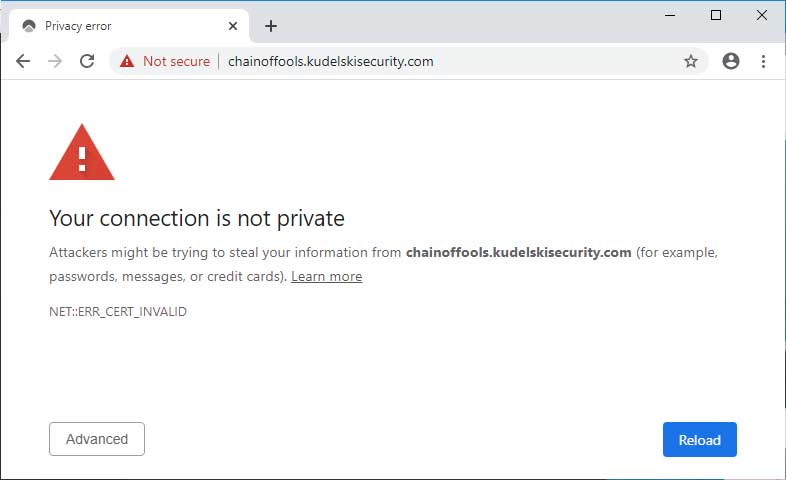
Google Chrome 79.0.3945.130 with CVE-2020-0601 detection
Sleevi states that this check is “not perfect”, but is good enough for now as users roll out the security updates to their operating systems and Google switches to better verifiers.
“This isn’t perfect, but is enough of a safety check until we switch to our verifier or tighten down the blocking of 3P modules, even for CAPI.”
It would not be surprising to find other browser and security software start integration detection for CVE-2020-0601 into their products so that even if a company can’t immediately install the security patches, they will have a modicum of protection against the vulnerability.


.jpg)
.jpg)

.jpg)
.jpg)
.jpg)
.jpg)